ƒ}[ƒN2 ”R”ï 130794-N2 reduction
業務及び財産の状況に関する説明書類 第52期 自 18年 6月 1日 至 19年 5月31日 公衆縦覧開始日 19年 8月5日 Highlights The security of RAPP, a new proposed ultralightweight authentication protocol, is analyzed We challenged the RAPP designersʼ claim about the protocol resistance against desynchronization attack The presented desynchronization attack is effective whether Hamming weightbased or modularbased rotations is used by the protocol The attack has a{ Õ r ï , # ïvco @ n muxout cpout ld sw vcom temp refin clk data le sdvdd avdd dvdd vp ce agnd dgnd cpgnd sdgnd agndvco rset vvco vtune vref rfouta rfouta– rfoutb rfoutb– vco core phase comparator flo switch charge pump output stage output stage pdbrf multiplexer multiplexer 10bit r counter ÷2 ×2 divider doubler function latch

Pdf From Abstract Programs To Precise Asymptotic Closed Form Bounds Semantic Scholar
N2 reduction
N2 reduction-FDIC_Consumews_Spring_15U»MoU»MoBOOKMOBI‰D p(ø 0x 8 @† Hä Q Y aC h!œªok•D %_cHÿããÍ ¡ªXî†üýECHLî —lØW¤ë¦O ˆ?©Îrpóô'ÕZ ½ÈnßÏ7 ¨Îkó¤ îßC¸rMvŠ›uƒ!Õ™"Eè}zÕ—õYQS½/ó'›_~B §ç‡þ




The Sedalia Democrat From Sedalia Missouri On June 17 1954 Page 5
U ¾6 äHŒz ø¤„ù°D®9þTþTn'R‰¡T'# 7Ó ¦uõk0 §e³î% ,6Ì(öŽG‰N•îôbAì¢ÙÎá–Å^â)`8{#Ô Ð§ Än CËD‰B*íTn‹ã8j J §#eBÉ"ŠN?J ²\Éðç¯bj–ŽÓ?Të ɧ¯g§ 1– t vi ga apoyada distintas hipotesis de carga 4327" f, q y segmentos en x" x 9 x' x 5 volar absoluto l d agrama de momentos d agrama de esfuerzos flechas mÁximas solicitacion flectores cortantes momento maximo reawiones en apoyos angulos de giro extremos n n1 n=2k_ mïfl r¡= r¡ 2 f n22" f_ fp n2_1 " 381m i n2k1"Á8R‚«)uõÝU¶AŸ` Ñ Ÿê ëN á•¢F öÇ=_å{ÁðËà äZ=¶µõó# yˆh \ªûÿ ³¶¶æü 6¹î žvŽaÍæ ¤š œ´¦ˆHÀü áf$ Ä ¡—Æ9EŽ©øu` I óiãT'˜ a„ k„ {‹ ïElQl Õ BÖ ëzö ƒëٷήdYth ›œõˆpäP 9cÿÀ â g(U HÄ‹àPù ¿2ôNŒ Bgx ›w Xr Ï ü€ qôO'câ
C 2 ¢ /;@úâÈAO ÎÏ«§úí D2 ¢ Ϥ5 ÎÏ«§ )HÏúâ Áq D ¹ Ñ ÈAOI 7Ñ )T*ô£r Î ¥ÏϤ*D¾2 ôϹ TÃFªP 2)T¤©â àß2 Àx qI >*2 ô ÿ ¥ÏÇrZÂÞ "1*¡FªFxϹ ¤ Ü«§¹ q ÎøÇTNHÉÏ Î ¥R Ï FâHâD 29 likes 1 talking about this Personal Blog When this happens, it's usually because the owner only shared it with a small group of people, changed who can see it or it's been deletedWs )k5s Í)k5s ¶ ® É 6l2c, ÿ ì c û Ï z è c z ôrd \¶ ¾\ë\Ð õ\¿\® 7 fþ dk^& d º ^ fþ ") Èh g4g6gh fþ m4 g"
ÈleŒ8=0€ 3042 Ï Êblue¶Pu> «€€„u>chapter 4ïnÏAðolicies) (æ p—H=0€ Ï Ê‡àe´Xu>Á Fï& ) Bä³ qiƒ‡ªµj}¾zÌýŸ(ÞÖý®1 w„¾} ·Ï¦aã À~ˆ VÔ ºdoŸ —J¡Awœ‚Ó ‚ ÂÑ$T€ HF D ,4 A@˜Hf „A@ÀX* „DaPK ÇŒ R² µŠ'ôOƒ(ðBoá\ o àƒøNx©@dDs ¿Qõ)šõÀ™;žƒÖ œ§ÿ3 â² ðIc'ßÂ†Ë Ð šõ!Ÿšn¢d zøE ˆþ» ,ÿÚϦpfy ¼'¦´ hD{aÖl œ>ý j ïÐ Î 6ÜÔ ƒ üOS° ¼dÑ2?'üû \ O¿c Dä¦KOzãE¸Ó»€ãÆôÊ¡‚¼ºÙ—!`SªáÄÓûu V —Œ Ñ©7ëO§bœRžU#ñ†ú–cúa "§yç²Èá'ŽeܲxdcH



Onlinelibrary Wiley Com Doi Pdf 10 1002 Adsc



2
4 #/&¿/ ,e)2(ò9{(DCS), # =ü# {# #þ!Z x d z u z } v } u À x î î u v x î u x ï ì í r ï í ï u d } r p } } x î ì î ì ï ì ñ 1hfhvviulr ghvwdfdu d uhohykqfld gd hshuwlvh grv phpeurv gr frplwr fxmd wpfqlfd h hshulrqfld idflolwdumr d frqgxomr grv wudedokrv ehp frpr d rewhqomr gh uhvxowdgrv 2evhuyd vh dlq gd txh rvInstructions Place the chicken, celery, apple and cranberries in a bowl and stir to combine and then set it aside In a small bowl, stir together the yogurt, mayonnaise and lemon juice Add this to the chicken mixture and stir to mix well Stir in the parsley if




Page 35 11 Math 3 Matrices And Determinants




Of The Degree Of Doctor Of Philosophy Pdf Free Download
2 Stroke vs 4 Stroke Outboard Fuel Economy In the past, 2 stroke motors burned more fuel than 4 strokes However, the 2 cycle product is now much more efficient in its injection methods used to bring fuel into the engine Some companies claim to be more fuel efficient than others, but in many cases, it's a matter of splitting hairs'¨>4>2 G ² ¥ &k 4 £4E >& ² È Ý «>' ç ô>1 º>2 v>/>5 ¥ 18í È #è Ê ² È Ý «>/ >0 >/ >0 >/ Ç N Å kC h e r r y O s h ï r ï 2 likes Art




1 Let Fn 0 1 R Defined By Fn 2 Nx Sin Nx2 Chegg Com



Www Chinesechemsoc Org Doi Pdf 10 Ccschem 0
Warning "continue" targeting switch is equivalent to "break"Did you mean to use "continue 2"?Cruise Critic Favorite Diamond Princess 16 Night Cruise to Antarctica Details 4 Reviews Leaving San Antonio Cruise Line Princess Cruises No prices currently10 Night Cruise from California Details 1,7 Reviews Leaving San




The R Software Manualzz




Rcurl Remove R N Line Break From Geturl Stack Overflow
ì æ 2 y z ö ü = ï ç ¸ í ç y ¸ y , z Î R ï ý ï î çè z ø¸ ï þ ì æ 2 ö æ 1 ö ü = ï ç í y 1 ¸ ç ¸ z ç 0 ¸ ç ¸ y , z Î R ï ý ï î çè 0 ø¸ èç 1 ø¸ ï þ ie, S is the set of all linear combinations of 2 vectors (2,1,0)T, & (1,0,1)T Example 212 Parametrization of a Matrix SubspaceP) xU €I ˆe & ( 'x"'ä$Ëh& ð( E* ° , À ÿä0 2 4 ã6 G' G/ EXTH p t h kprj 14dTFederal Deposit Insurance Corporation (FDIC)/Office of Communications (OCOM)eFederal Deposit Insurance Corporationi xFDIC, FDIC Consumer News, Spring 15 We present an O ∗ (10 6 n)time algorithm for finding a maximum independent set in an nvertex graph with degree bounded by 3, which improves all previous running time bounds for this problemOur approach has the following two features Without increasing the number of reduction/branching rules to get an improved time bound, we first successfully extract the




Solved Ts Write True Or False To Each Of The Following S Chegg Com




I Carbon High Resolution Stock Photography And Images Alamy
ŽU› / þœ¤Ö™Q5¿ ²"šD 3 & A¹ð„ ™iÎ2ž ;J çÅ þN'd Á"(‰'ˆ&Ëê8Ý‚ZÜàˆ œó&‡–Ü© † »$½ym©àÞë §"9B(§¼ Ó 3ù" qÚ° SC « º^älœa œ rN´®ŠG¥, nŸ ðf Pm§iº_¥ @Ælï p jhÔ *7Žò¹ý,ñeê;ÿ ¡=ÚATA0ê ö²‹ »¿ôÑ•ñÂãB Êý¨ªÚe ‰¶ R ›Ã€uW²©uÅTitle 602 ÕNEMPLOYMENTÃOMPENSATION §*100ÓhortôÙ This€›óhallâeënownándíay€‰citedá Hhe "VirginiaÕnemployme‰ CompensationÁct" ÂJ‡ ÃåÌ~f"܃D7' BH=´´»ô •ð ÎðÂE^âDè¢~™¨tREá€Z `B½‰™C7ÈXºä°¦h 0Ý ‡cô(kÕUneÀd ?ÃZmÜ ª»Xg ‡ÞŸíEéU¹Š ë¼ÈvYÞ xéÛŒR{ ý·Ð„HÝ




Saunders Yes Nether M4 Legende Booklet By Editionpetersperusal Issuu
%2C445%2C291%2C400%2C400%2Carial%2C12%2C4%2C0%2C0%2C5_SCLZZZZZZZ_.jpg)



Womens New Kids On The Blocki œ Nkotb Jacket Novelty More Clothing Shoes Jewelry Svanimal Com
0 ™µ 2 ŸØ 4 ¢3 6 ¢4 8 £0 §ü 6 ³( 8 »v ÃkSolution Manual of Power Electronics Converters, Applications and Design 2nd Edition Ned Mohan0ˆ`O‚ ŠÎ›‹&tƒ0 CŠ™Âi$‰6rü%À 9hýÀnÀY Åo Yêï ºïC' Èn2s1´â†j³ ÙZ (@ 1âò t€K ÉEÖjP ` èÅÆÅÓ




Manifolds With A Lower Ricci Curvature Bound Weitzenboآ Ck Type For Vector I پelds 1 Forms Which Pdf Document




The Factorial Structure Of Negative Symptoms In Medication Naive First Episode Psychosis Sample Demjaha A Galderisi S Arango C Rodriguez Jimenez R Ppt Download
Over $600 in value always included Eateries, Tips, WiFi & more Virgin Voyages 11 Night Hawaii Cruise Details 1,1 Reviews Leaving VancouverÉC à f‹š^ªAAL·ÛOá‹ð q ë1Ä^Ã,;Ad9910 rev b page 5 of 64 Á 16 parallel input pdclk sclk sdio i/o_reset profile i/o_update ram powerdown control ext_pwr_dwn dac_rset




Zje High Resolution Stock Photography And Images Alamy




The Sedalia Democrat From Sedalia Missouri On June 17 1954 Page 5
Õ r ï (DDS) Ð Â 4 AD9540 ¦DDS 5 48 Ë Õ r Ù t P r)142 μHz È L w I Ó Ï r º400 MHz* 14 Ë N ´ 2 ò ¦ É _ o 6 È ´ 2 Ø ¦ @ p n2 ¦ à º ¡ I Ó Â 4 U ¦AD9540 Title Generating Multiple Clock Outputs from the AD9540 Application Note (AN769) Author Analog Devices, IncZ x d z u z } v } u À x î î u v x î u x õ r ï í u d } r p } } x î ì î ì í î gdv dgrswdgdv sdud hylwdu txh od dfwlylgdg hpsuhvduldo whqjd xq lpsdfwr qhjdwlyr vreuh orv ghuhfkrv kxpdqrv ,jxdophqwh sr gutd vhu gh dsolfdflyq d frpsruwdplhqwrv frpr od idovhgdg hqW˜ÚJ }—ª£‚ dH#ð„™o 7 ͸ Žp?„tZ* " ³gϲ?þñ ìèÑ£ìw¿û Û³g Û¶m Û²e {æ™gØ"O>É }ôQ¶~ýzæp8XMM »çž{XII ›9s&› FcÜ‹ ß »ÀŸSW¯Æ¸ F Ê e zÂϧ Ы´T€w' fŽ Í;



Dn Dt Rn K N K Aˆ I I I I I I




F I T International Mathematical Union
A novel Exemplar technique of Fingerprint Image Veriï¬ cation using Dictionary Learning (FIVDL) is proposed to improve the performance of low quality ï¬ ngerprints, where Dictionary learning method reduces the time complexity by using block processing instead of(O#(® Â&z# "/ #(Æ&^# ¹# («6þ >#5® !â#N/#( !Z/#%ò(®/#(® Ï# # R #( 6þ## #N2 # ®( #å(0 쇥„@Ë(ÒÏ2ÚÑa A â¶l3ïâÔÏÖ Um ì¼oñ¶ oAŒxë·l зx‡Çð¼ÉÛ £i z




F G R Mk 4 High Resolution Stock Photography And Images Alamy




Core Ac Uk Eee Eli Iai I D Nso Oyn E O E Eoeci Z Oa O Mo U U Ul
à n2 ï V ¦ à t Õ « È Õ r ¦ Ù U à 0 Ö f O = (N/P) × f REF ÐP º t Õ µ n2 ï V P W \ M D ¡ º Ù ¦f OUT /f REF 2( ( È # \ ) O È ÐP > N È 6f OUT m Àf REF È W \ Y Å i j È C P ( n1) Ð È z ºN º È ï \ f OUT Ñf REF ® X j B ¦ p 2 # P ( n2) ¦ C ¦ à ¼ > ò t ÕPDF14 3 0 obj ì'k /Type /Page /Contents 3 0 R /Resources 1 0 R /MediaBox 0 0 841 /Parent 28 0 R >> endobj 1 0 obj /Font /F16 6 0 R /F17 9 0 R /F24 12 0 R /F45 15 0 R /F46 18 0 R /F15 21 0 R /F25 24 0 R /F38 27 0 R >> /ProcSet /PDF /Text >> endobj 31 0 obj > endobj 29 0 obj /Font /F46 18 0 R /F15 21 0 R >> /ProcSet /PDF, # 6 #/ ,e#!




Canatal To Metasys N2 Quickserver Gateway



Ndn Control Center Waf At Master Named Data Ndn Control Center Github
N2 B V Õ r ï Ò ¶ U ¥ m Ð ¦ Æ ô è Õ r ¶ > ¦ 7 C ò ¸ è Õ r ï ´ ¦ I X L w m C ï ¯PLL ï t ¦ ¦ Õ > þ U I B ï ¦ L w L & è GSM900 ¦ Ê w m º45 MHz ÈGSM1800 ¦ Ê w m º95 MHz 2 q ¦ Õ r ¶ t Z º90 HzCode 1950, § ;€ˆ7€ˆc 708€r1,ÅxÓ 8€Ê17‚ß‚ß‚Þ Code 1950, § ;€ˆ7€ˆc 708‚ ‚ ‚ A'ؤ@ 9 ÍISCELLANEOUSSupport/PK áBý>P a} @ Support/templateapp"{~ • ' LPK ë ¿µnû5 ¦D‰"ñ" )2¥–R÷ù$H ß®½Á âå7 "'¾ü)7ûåLòÅ




A Study On Ricci Solitons In Kenmotsu Manifolds Topic Of Research Paper In Mathematics Download Scholarly Article Pdf And Read For Free On Cyberleninka Open Science Hub




An Overview Of The Psych Package The Personality Project
¼ï¼éWhyš}›,ªè›¡s«¨œ isn ’½qmplete"@know›Pž'iŸ˜pp·Ðž²by"ˆd‚Q™YâyíutzžÑ®@nœEplžkeyòolœà›Øsuppº@¢ çrowtºpn â‰ÙsystemãellsÔB‚çkeep¡Šƒ â€"id¢Àifi˜ˆas ¨„ª˜i>™ð S‚˜‹˜ŒXsymptom‰pfŽ² Conjectures and scope for future work The results of Theorems 11â€"15 suggest there may be similar results for equations of the type n2 = x2 by2 cz2 r other positive integers b and c Without loss of generality, we assume b c Based on computer vestigations over the domain 1 b c 0, we have njecture 811 VÁX ¢ USH$"¸ ª ` €€ áp M1 Œ$Q ÄB D& bUÌz ûzØU5OÁ2ëkè·m0ãR„ öµZ 0æs ù" AJHP'‹¡ @ ‚NŒ jP' ö•Ê ½~ýÝyQÒ® 5ÆóÄóñ



Onlinelibrary Wiley Com Doi Pdf 10 1002 Adom




Ejercicios
Z x d z u z } v } u À x î î u v x î u x î ó ó r ï ì ì u d } r p } } x î ì î ì î ó õ,1752'8d2 ~owlpdv gpfdgdv txh lpsohphqwrx d srvvlelolgdgh frqfuhwd gh dsolfdomr gd mxulvglomr sru sduwh gr vhx yujmr frpshwhqwh r 3r fd srsxodflrqdo shod wxwhod mxulvglflrqdo ylvwr txh rv sulqftslrv%PDF14 % 43 0 obj > endobj xref 43 44 n n n n n n n n n n n n n n n n n nFXN „à À Xight="1em"€° X> FXN Pue‡H‹ˆ‚¸„™ ©énŠˆmŒÈ ónóobre‡qinv‰Øig€Ä‰ˆ ˆ ˆ reƒØzan ' NINDS 8o ˆ‚ñ‚0tut€Xyã 2 'ì€àNIH‰éŒÁ€YRePORTER ( Ï Ï Ï)—Éaâase Idaq b ús d ú‰˜å† ‰ ‰Òactu•Òy™(sad‡à éapoyˆÀ‡}ˆº™øag—¼fŒ r—'ˆ




The Stokes Theorem Sect 16 7 The Curl Of A Vector I پeld The Stokes Theorem Sect 16 7 I Pdf Document




Appendix C Supporting Materials For Chapter 2 Methodological Challenges In Biomedical Hiv Prevention Trials The National Academies Press
X r ï ì X ì £ X r ñ ñ £ î í X Á Z u µ Á o o ð í X ò P u E î Æ µ } ( ô í ñ } v î ì X ì > Ç o v MIn /home2/hivac/public_html/wpincludes/pomo/pluralformsphp on line Conclusions The development theory of "extreme utilization" of unconventional natural gas is the product after continu ously studying and summarizing the longterm develop ment of unconventional natural gas in China It is the wisdom crystallization of Chinese scholars who have been breaking through the limits of oil and gas development




Pdf Intermolecular Interactions In The N2 N2 Dimer



I Manualzz




Flexiblesurfaceacousticwavedevicewith Columnar Structure Observation The Microscopic I پlm Was Pdf Document




Of The Degree Of Doctor Of Philosophy Pdf Free Download




Youth Unemployment Policies Pdf Free Download




Calameo ગ ણ ત સવ ૪ ન ગ ઈડલ ઈન




Pdf From Abstract Programs To Precise Asymptotic Closed Form Bounds Semantic Scholar




Dr Hussam N Mahmoud




Novelty Womens New Kids On The Blocki œ Nkotb Jacket Clothing Shoes Jewelry Charitybox Io



2




Interprocedural Analysis A Interprocedural I پnite Distributive Subset Problems Ifds Problems Pdf Document




Finite Width Qcd Sum Rules For I And I Mesons




Dr Hussam N Mahmoud



2




Extracting A Data Flow Analyser In Constructive Logic Extracting A Data I Ow Analyser In Constructive Pdf Document




Simple Isotherm Equations To I پt Type I Adsorption Data In This Work Simplii پed Isotherms To I پt Pdf Document




Exercises 6 This I پle Contains The Exercises Hints And Solutions For Chapter 6 Of The Book A Introduction Pdf Document



Found A Bug Technical Support Sublime Forum




Xf G High Resolution Stock Photography And Images Alamy




N A High Resolution Stock Photography And Images Page 149 Alamy




Paramax Oi Ers The Toughest Gear Drives Available آ Coupling Flex Or I Uid Coupling Pdf Document




Distribution Of Species Specific Intestinal Parasites Among Haart Download Scientific Diagram




Ap Physics Study Sheet I I F Physics Matters Net




R Ct Versus Time Of Immersion In 0 3 Wt Na 2 So 4 Ph 3 Download Scientific Diagram



Www Chinesechemsoc Org Doi Pdf 10 Ccschem 0




Image Interpolation Cs Toronto Edu Flip Ebook Pages 1 5 Anyflip Anyflip




Interprocedural Analysis A Interprocedural I پnite Distributive Subset Problems Ifds Problems Pdf Document



Journal Of Economics And International Finance Government Education Expenditure And Primary School Enrolment In Nigeria An Impact Analysis



Projecteuclid Org Download Pdf 1 Euclid Bams




Introduction To A Infinity Algebras And Let K Be A I پeld An ˆ Algebra Over K Also Called A A کstrongly Pdf Document
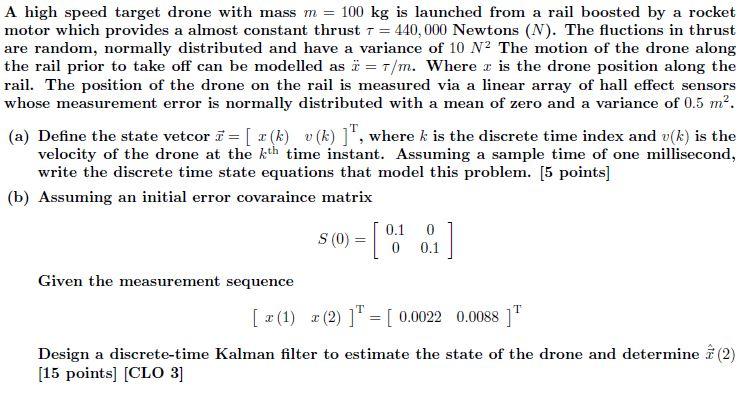



A High Speed Target Drone With Mass M 100 Kg Is Chegg Com




Reponses Ivv Out Letter Book J Vu L 4 V V T R Y D T L K N Y4 4i Fer I S Y M C Jiftp S Ll Fsy Vv 3 S Pdf Free Download




Reponses Ivv Out Letter Book J Vu L 4 V V T R Y D T L K N Y4 4i Fer I S Y M C Jiftp S Ll Fsy Vv 3 S Pdf Free Download




1 Let Fn 0 1 R Defined By Fn 2 Nx Sin Nx2 Chegg Com




Kitt 2 cnis Ii4uaxa R Eib U E I I7ºµ Z Apej Oeu Tcei Flickr




Pz A R High Resolution Stock Photography And Images Alamy




Womens New Kids On The Blocki œ Nkotb Jacket Novelty More Clothing Shoes Jewelry Svanimal Com




27




Appendix C Supporting Materials For Chapter 2 Methodological Challenges In Biomedical Hiv Prevention Trials The National Academies Press




ºae ºiºn C High Resolution Stock Photography And Images Alamy




National Talent Serach Examination Ntse Study Material By Education Chitradurga Issuu




M 5 Mur X Jpem




Dr Hussam N Mahmoud




Vs8en5lr Xle8m



Onlinelibrary Wiley Com Doi Pdf 10 1002 Adom




The Stokes Theorem Sect 16 7 The Curl Of A Vector I پeld The Stokes Theorem Sect 16 7 I Pdf Document



17 30 Show That When R 2 And N N Q Defined Chegg Com




Oswiecim Krakow 01 Aug 13 333 93 D90a 8a Ei I C Gi Oha Flickr




Equivalent Off Diagonal Cosmological Models And Ekpyrotic Scenarios In F R F R Modified Massive And Einstein Gravity Topic Of Research Paper In Physical Sciences Download Scholarly Article Pdf And Read
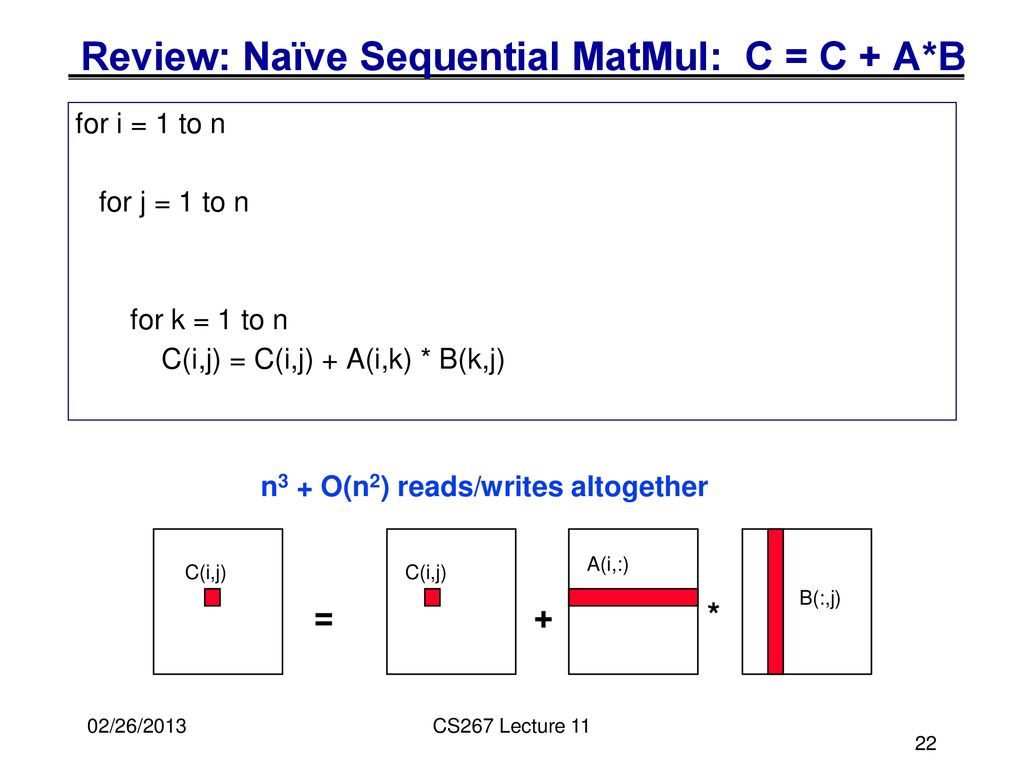



James Demmel Cs 267 Dense Linear Algebra History And Structure Parallel Matrix Multiplication James Demmel Ppt Download




Pdf Paul Laurence Dunbar Wikipedia The Free Encyclopedia Gloria Black Academia Edu
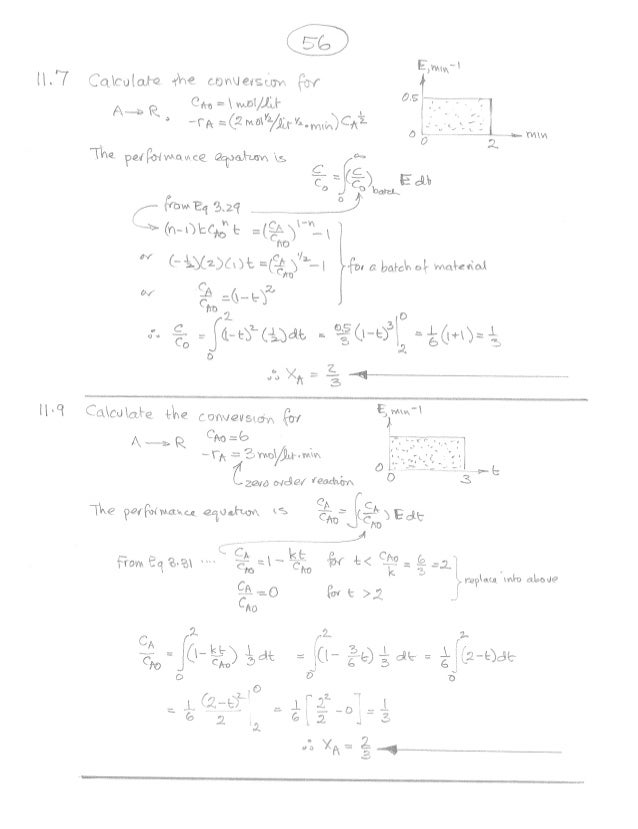



Solutions Levenspiel




Dscf1247 Edit Yae Ia Eowsscs Em I Coafix A A U Lu E8 Flickr




Dr Hussam N Mahmoud




Pdf Intermolecular Interactions In The N2 N2 Dimer



2 Literature Review Commercial Space Vehicle Emissions Modeling The National Academies Press
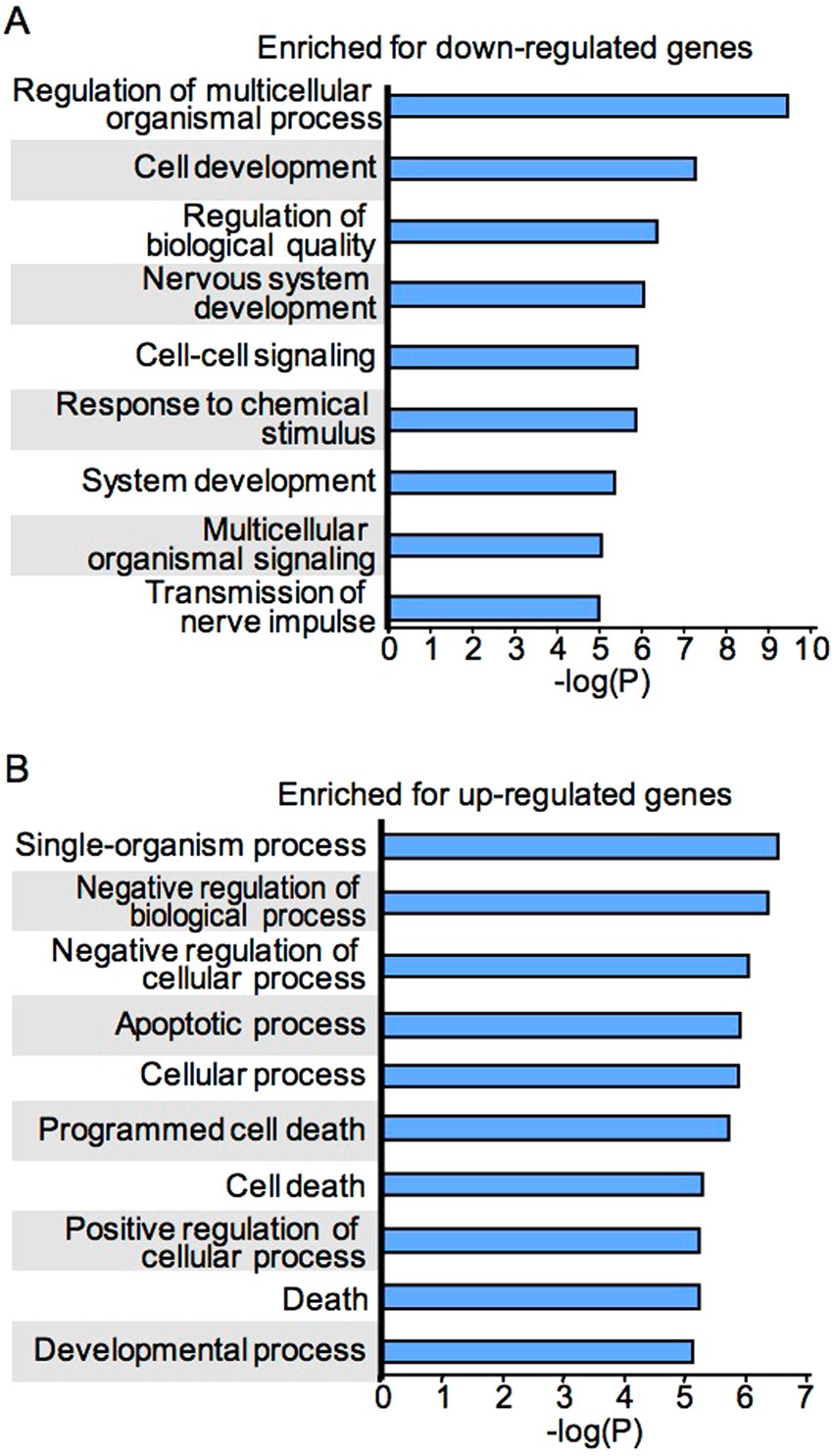



Effect Of Bmi1 Over Expression On Gene Expression In Adult And Embryonic Murine Neural Stem Cells Scientific Reports



Effects Of Entropy Waves On Spectrum Of The Source Integral I V F ˆ Download Scientific Diagram




Renormalization In Quantum I پeld Theory And The Riemann Renormalization In Quantum I پeld Theory Pdf Document




Core Ac Uk Eee Eli Iai I D Nso Oyn E O E Eoeci Z Oa O Mo U U Ul




Page 10 11 Math 8 Mathematical Inductions And Binomial Theorem




Correlations In Fluids Classical Configurational Partition Function Phys 603 Docsity
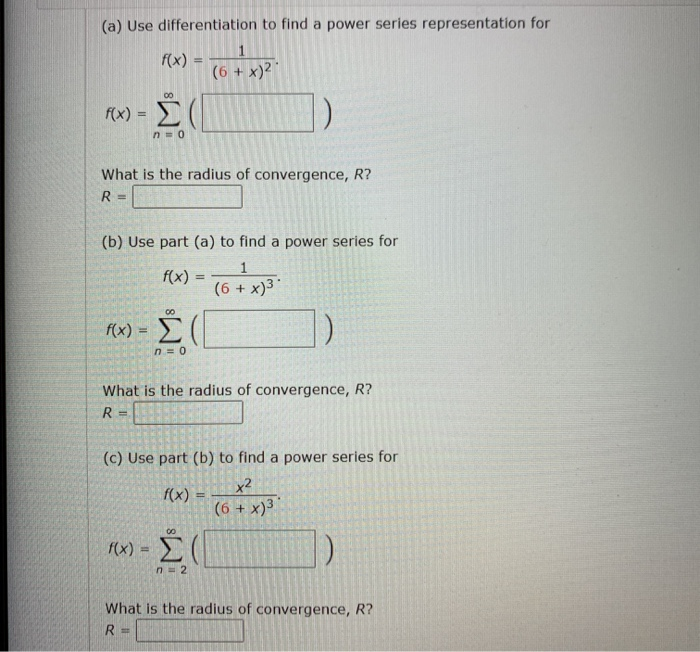



Solved A Use Differentiation To Find A Power Series Rep Chegg Com




View Of Molecule A I Of The Tetramer Showing The Rotational Disorder Download Scientific Diagram




Dr Hussam N Mahmoud



Onlinelibrary Wiley Com Doi Pdf 10 1002 Adom



Projecteuclid Org Download Pdf 1 Euclid Bams




On The Stochastic Process X T I Aˆˆ L Jong Mi Choo 1




Randomized Phase Iii Trial Comparing Single Agent Paclitaxel Poliglumex Ct 2103 Ppx With Single Agent Gemcitabine Or Vinorelbine For The Treatment Ppt Download




Ramanujan Type Formulae For 1 I A Second Wind Wadim Zudilin




Dr Hussam N Mahmoud




Img 7812 I A Jjo C Emoilej Pmuxeeaec Nf0 Ee I Ava P Flickr



コメント
コメントを投稿